Cyber Security is a term used for the collection of methods to protect an organization’s confidentiality, integrity, and availability of data from external and internal threats. Cyber Security includes the security of the application, data, network, mobile, and cloud [1]. Companies across all sectors have experienced cyber-attacks as COVID-19 forced the whole world to restructure the way of working and cyber security strategies. Some of the major vulnerabilities reported this year as mentioned in the cyber 2021 report are [2]:
- The Achilles family of vulnerabilities revealed more than 400 weaknesses in a Qualcomm chip that affects a large portion of the entire mobile market.
- Instagram was reported to have an RCE zero-click vulnerability in its JPEG decoder. A few are detected in WhatsApp and Facebook also.
- Apple’s ‘sign in’ system vulnerability can allow remote attackers to bypass authentication and take over targeted accounts.
To close the gaps, companies are looking for optimum solutions. Blockchain can be seen as one of the recommendations to prevent cyber-attacks.
| Sector | Use of Blockchain | Impact |
| MOBILECOIN (Software Company in San Francisco, California) | Uses Cryptocurrency to keep all transactional data between two peers encrypted and transparent in the public sphere. | They design their product to be easily integrated with WhatsApp, Facebook Messenger, and Signal. |
| SANTANDER (Bank in Boston, Massachusetts) | The bank’s blockchain enables customers to securely pay between Santander accounts in Europe and South America. | The bank is developing a voting mechanism through which decentralized votes are incorruptible and in real-time. |
| Hashed Health (Healthcare Firm in Nashville, Tennessee) | The firm has worked with dozens of healthcare companies and hospitals to build secure digital blockchain networks for patient information sharing and internal communication channels | It improves quality measures and payment efficiency for hospitals and healthcare systems across the U.S. |
| Government IN The State of Colorado | The Colorado Senate passed a bill in May 2018 to consider blockchain for data protection and the secure storage of records. | They are looking to pass more bills involving the uniform definition of a “token.” |
| Defense Advanced Research Projects Agency in Arlington County, Virginia | Defense is looking into blockchain mainly for its usefulness in encryption and secure data transfer. | It is created for military personnel to share information to any location on the globe without getting hacked. |
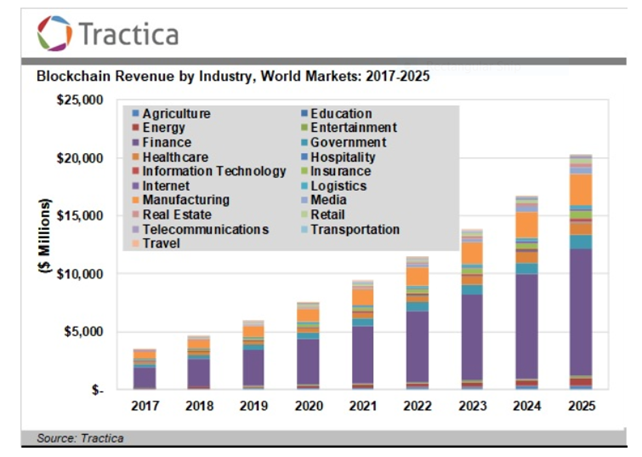
Blockchain can help in real-time prevention in most of the sectors by copping up with the Relentless and Clever attacks as shown in Table 1 and Figure 1. Real-Time Prevention places the organization in a better position against any cyber-attack which is quite evident from the examples listed above and the investment report by Tractica report.
Use cases for Cyber Security
Blockchain can be considered as the recommendation for cyber security as it can resolve the following use cases:
- To reduce the chances of systems getting infected during downloads and updates with malware, Blockchain allows users to compare the hash of updates and available downloads (to be downloaded) with the developer’s hash.
- With the decentralizing feature of blockchain DDOS attacks can be restricted as it works more like a distributed network and traffic on a particular over route can be handled.
- Blockchain can help social media users to get rid of the burden of changing the password frequently as it relies on biometric data, private keys, and multistep authentication
How to integrate blockchain?
The basic of blockchain revolves around blocks which are created for every new entry made during any transaction. Later, rather than storing it in a centralized place, each node is going to have a copy of it. It works as a peer-to-peer network. It is like entering the data on a sheet that anyone can see but no one can update. Each node in the network requires to approve that transaction and can able to see that change. While trying to integrate it into existing projects there are some pre-requisites that are to be done as listed below [4]:
- Hiring an experienced blockchain developer
- Do we need a crypto token?
- Shall we go for public (permissionless) or private(permissioned) blockchain?
- Which framework to choose?
- How to host a blockchain network?
The commonly used blockchain platforms in 2021 are Mist, Truffle, Ether-Scripter, Tierion. Few platforms allow the use of Java, Kotlin, etc but for others, an expert is required who can use languages like solidity and simplicity.
Other Recommendations for cyber security [2]
- Threat Intelligence: It uses information from multiple sources and comes out with the most effective solution for the network. By covering all the entry points in the network, threat intelligence proving to be an essential security tool for companies.
- Real-Time Prevention: It means to prevent cyber-attacks before they breach a system. Companies need to stress the prevention of the unknown to win the battle of cyber security through some practical approaches [2].
- Secure your Everything: Every part of the blockchain matters. Companies need to check the security level and relevance of all network infrastructures and processes, as well as the compliance of connected mobile, IoT, and endpoint devices.
It is important for every individual who is a part of the software industry, to be updated with the latest trends in cyber security through relevant sources.
How AgBe handles security issues?
The web applications that we designed, are implemented with effective planning by the Engineering team. We follow secure coding principles as described in OWASP (Open Web Application Security Project). Of those secure coding concepts, the best practices that we follow to protect against vulnerabilities are:
- Restricted Unauthorized Access to PII like email, contact number, and DOB
- Providing secured Direct Object Reference like during video calls, documentation sharing, etc
- Not Disclosing EXIF Geolocation Data
- Rate Limit Implementation while signup, sign-in, generating otps, etc
- Providing Email ID and Phone No. verification if someone tries to update the user detail
- Planned Password Management like Storing only cryptographic hashes of passwords rather than plain texts
- By implementing loggings of failures, errors, and exceptions
- By avoiding sequential or predictable ids
AgBe Labs is continuously investing in Blockchain technologies to innovate secure and viable solutions to business problems.
References